The Amplification Files - Week 2: The Frankfurt Stock Exchange
This is Week 2 of The Amplification Files where The Coalition of Cyber Investigators tell the story of how a boiler room investment scam operation was able to credentialise itself on one of the most respected sources of financial information in Europe - The Frankfurt Stock Exchange.
Paul Wright, Neal Ysart & Lajos Antal
10/8/20254 min read


The Amplification Files: Week 2
The Frankfurt Stock Exchange
When Fraud Was Amplified in Frankfurt
Fraud depends on borrowed trust. It doesn’t matter where the operation is registered, what telephone number it uses, or how amateurish or polished the website appears. If the name appears on a reputable financial platform, that borrowed trust is enough to deceive many people into taking it seriously.
As our first case demonstrated in London, criminals using the hijacked name Penn Park Capital Management Limited managed to appear on the London Stock Exchange’s RNS. However, the scam did not end there. Across Europe, the same scheme emerged within one of the continent’s key markets: the Frankfurt Stock Exchange (Deutsche Börse).
What happened
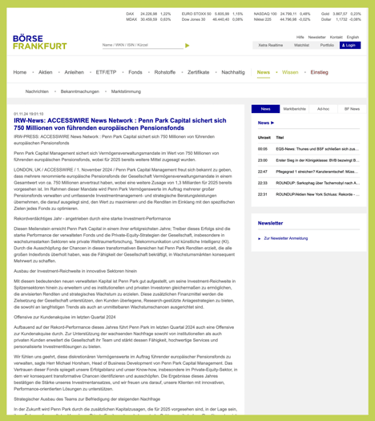
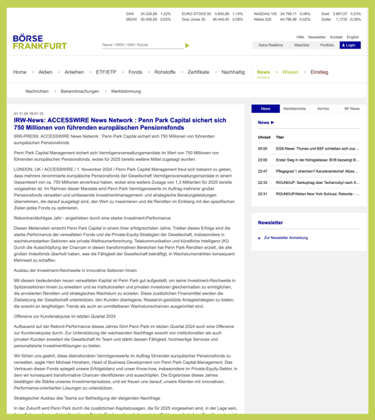
The culprit remains the same: a fake Penn Park Capital Management, which hides behind the stolen name of a legitimate business and pretends to be Europe’s leading fund manager, managed to get a bogus press release published in Frankfurt. On the surface, this announcement appeared no different from updates issued by blue-chip companies and greatly helped to credentialise them.
But as we know from the London Stock Exchange incident, the firm behind it wasn’t authorised. They had no approval from any European regulators, no standing in Germany, and no right to sell investments to anyone.
In this case, it appears that the bogus release did not arrive directly. Instead, it is likely to have travelled the following path:
Step 1 – Accesswire: the newswire service accepted and distributed the fraudulent release.
Step 2 – IRW‑NEWS: having ingested Accesswire’s feed, IRW‑NEWS re‑syndicated the material into Germany.
Step 3 – Frankfurt Stock Exchange: through its partnership with IRW‑NEWS, the release appeared inside Deutsche Börse’s own distribution environment.
On screen, the release appeared like any other corporate update. The mechanics behind it remained unseen by victims. All they saw was the Frankfurt Stock Exchange carrying the announcement. That was all the credibility the scammers needed.
The problem with disclaimers
As in London, disclaimers acted as a corporate safety net.
At each stage of this relay, there are disclaimers.
Accesswire disclaims responsibility for content.
IRW‑NEWS repeats the disclaimer.
Deutsche Börse’s Frankfurt Stock Exchange does not take responsibility for content published on its platform.
Legally, these disclaimers protect the organisations involved. Practically, it doesn’t prevent investors from believing what they’re reading.
When you see a press release on the Frankfurt Stock Exchange’s platform, the natural assumption is that it’s not criminals behind it. The brand of the exchange gives weight to the words, which is exactly what a scammer wants.
Duty of care
The gap here is simple. Exchanges don’t need to vet every sentence, but they do need to stop publishing materials from firms that have no regulatory standing. A quick database check with BaFin, ESMA, or another relevant authority would be enough, and this could have been done at Accesswire upstream, or at IRW‑NEWS before re‑syndication, or at Deutsche Börse itself.
There’s a clear difference between true neutrality and negligence; however, neutrality shouldn’t permit criminals to credentialise themselves, making it easier for them to deceive victims.


Why this matters
The Frankfurt Stock Exchange's reach is global. Announcements here ripple outward into countless feeds and services. A single fraudulent press notice, once live, multiplies fast. By the time anyone realises, it’s already been noted down in analysts’ spreadsheets, media coverage, and investor tip sheets.
Fraud thrives on that kind of amplification. And every time an exchange or news outlet gives the stage to boiler room investment fraudsters, their credibility gets stronger.
What must change
The fix remains modest.
For all entities involved in the process, there should be a duty of care to help prevent any publication pathway for bogus firms. Mandatory screening against official databases, combined with basic due diligence, would have quickly uncovered that the fake fund manager was not licensed in any of the countries they claimed to operate in. There can be no clearer red flag.
Disclaimers alone are not a comprehensive strategy to protect consumers. If the platforms that form the foundation of Europe’s financial system wish to maintain trust, they must treat duty of care as more than just a phrase in a policy document.
Authored by: The Coalition of Cyber Investigators
©2025 The Coalition of Cyber Investigators. All rights reserved.
The Coalition of Cyber Investigators is a collaboration between
Paul Wright (United Kingdom) - Experienced Cybercrime, Intelligence (OSINT & HUMINT) and Digital Forensics Investigator;
Neal Ysart (Philippines) - Elite Investigator & Strategic Risk Advisor, Ex-Big 4 Forensic Leader; and
Lajos Antal (Hungary) Highly Experienced Cyber Forensics, Investigations and Cybercrime Expert.
The Coalition unites leading experts to deliver cutting edge research, OSINT, Investigations & Cybercrime Advisory Services worldwide.
Our two co-founders, Paul Wright and Neal Ysart, offer over 80 years of combined professional experience. Their careers span law enforcement, cyber investigations, open source intelligence, risk management, and strategic advisory roles across multiple continents.
They have been instrumental in setting formative legal precedents and stated cases in cybercrime investigations, as well as contributing to the development of globally accepted guidance and standards for handling digital evidence.
Their leadership and expertise form the foundation of the Coalition’s commitment to excellence and ethical practice.
Alongside them, Lajos Antal, a founding member of our Boiler Room Investment Fraud Practice, brings deep expertise in cybercrime investigations, digital forensics and cyber response, further strengthening our team’s capabilities and reach.